HTB Academy Module Notes
Date
11.27.23
Objectives
- Conduct simple network enumeration while service scanning on web servers.
Key Concepts
- Network Enumeration using automated fuzzing tools.
Tools and Techniques
- Gobuster: A tool for directory enumeration. It helps in finding hidden pages and functionality that can expose sensitive data or escalate privileges. It is used for DNS, Vhost, and directory brute-forcing and can enumerate public AWS S3 buckets. We will focus on directory brute-forcing using the
dirswitch.
Practical Exercises
- Performed a simple scan with Gobuster using the
dirswitch and thecommon.txtwordlist from dirb. - Example Gobuster command and output:
gobuster dir -u http://10.10.10.121/ -w /usr/share/dirb/wordlists/common.txt - Key HTTP Status Codes:
200: Resource request successful.403: Forbidden access to resource.301: Redirect (not a failure).
- Notable Finding: A WordPress directory present on the server (http://10.10.10.121/wordpress), indicating a potential vulnerability.
DNS Enumeration
- Subdomains can reveal resources like admin panels, exploitable applications.
- Used Gobuster in DNS mode for subdomain enumeration.
- The
dnsflag specifies DNS modes. - Example Gobuster command for DNS enumeration:
gobuster dns -d inlanefreight.com -w /usr/share/SecLists/Discovery/DNS/namelist.txt
gobuster dir -u http://10.10.10.121/ -w /usr/share/dirb/wordlists/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.121/
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/12/11 21:47:25 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htpasswd (Status: 403)
/.htaccess (Status: 403)
/index.php (Status: 200)
/server-status (Status: 403)
/wordpress (Status: 301)
===============================================================
2020/12/11 21:47:46 Finished
===============================================================
Using SecLists
- SecList: A collection of data sets for automated vulnerability scanning (fuzzing).
- Installation commands:
git clone https://github.com/danielmiessler/SecLists sudo apt install seclists -y - Added a DNS server (e.g., 1.1.1.1) to
/etc/resolv.conffor network-related testing.
Banner Grabbing
- Using ‘curl’ to grab server headers.
- Example
curlcommand:
curl -IL https://www.inlanefreight.com
Utilizing EyeWitness and WhatWeb
- EyeWitness and WhatWeb: Tools for capturing website screenshots, header info, and identifying default credentials or web server versions.
- Example WhatWeb command:
whatweb 10.10.10.121
Key Takeaways
-
Understanding web directory structures is crucial for identifying vulnerabilities.
-
The
robots.txtfile can provide clues to hidden directories. -
The automation provided by SecList is highly beneficial.
Okay so I had to figure out how to capture the flag here. I used the robots.txt file to see what domains were disallowed to be crawled online. That clue was enough to check the url.
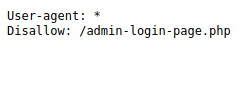
I tried 94.237.53.58:/45327/admin-login-page.php and we got a login page.Then looked at the source code of the webpage to see if there was any details. Using CTRL + U on the web browser, it can also be done using curl chained with grep to find any common words such as password.
Questions and Curiosities
- Curious about the mechanics of HTTP header fetching and redirection.
- Interested in further understanding DNS functionality, especially the impact of adding a server to
/etc/resolv.conf.
Additional Resources
Personal Reflection
- Challenging because I had to opt out of just using the terminal to explore possible vulnerabilities.

